Linux Generate Cert.pem Key.pem
- Linux Generate Cert.pem Key.pem In Hindi
- Pem Definition
- Linux Generate Cert.pem Key.pem File
- Linux Generate Cert.pem Key.pem Free
The self-signed certificates delivered with your MySQL Enterprise Monitor installation are set to expire after 365 days. Every upgrade is delivered with new certificates set to expire 365 days after the day the upgrade package was built. In the unlikely event you are running a version of MySQL Enterprise Service Manager using the default certificates for more than a year, you must generate new certificates. If you do not generate new certificates, the SSL connection between MySQL Enterprise Service Manager and the repository fails. This section describes how to generate those certificates.
These instructions guide you through the process of installing SSL certificates for your MySQL Enterprise Monitor installation. The $INSTALL_ROOT represents the root path of your installation, which defaults to:
Table 6.1 Default Root Path ($INSTALL_ROOT)
| Operating System | Default Path |
|---|---|
| Microsoft Windows | C:Program FilesMySQLEnterpriseMonitor |
| Linux / Solaris | /opt/mysql/enterprise/monitor/ |
| Mac OS X | /Applications/mysql/enterprise/monitor/ |
Jan 25, 2016 Create PEM file for your Linux server Objective: To disable password based logins and login only using key based authentication. Will create a pem file which will be used to access the server. OS used is CentOS 7 64bit. Read instructions on how to create different.pem files for three different scenarios. Learn more about the installation process here. Creating a.pem File for SSL Certificate Installations. Converting PFX File to.Pem file using OpenSSL in Windows 10, Some Application never allow.pfx file to import directly. Running Ubuntu Bash shell become much simpler in Windows 10In Windows 10 you can have a linux subsystem. It’s a great feature for sys admins for these sort of tasks.Start – Run – Appwiz.cpl – Turn Windows Features on or off. Dec 21, 2010 If Firesheep and other menaces have you freaked out about using unsecured connections, it’s time to take matters into your own hands. In just under 20 minutes, you can create a self-signed certificate for Apache to connect to your Web site for passing any kind of sensitive information. It’s easy and takes very little. May 05, 2019 Pem file is a private file which do generate via ssh-keygen on linux server. Impotent:- You need to backup old key files if you have old keys server. 1st create the keys and RSA will create public and private keys. If you no need add passphrase on your key then you can add passphrase with key but I skipped the passphrase on server.
To use SSL, you must generate a certificate and private key. These can be verified and signed through a third-party authority, such as Thawte or Entrust, or generated locally and self-signed. The recommended tool for locally-generated SSL key and certificates is the OpenSSL Toolkit. The OpenSSL libraries are delivered by default with UNIX, Linux and Mac OS X platforms, but must be obtained separately for Microsoft Windows from http://slproweb.com/products/Win32OpenSSL.html. The Windows installation also requires the Visual C++ 2008 Redistributables libraries.
For security reasons, we recommend you install the latest, compatible version of the OpenSSL Toolkit.
If you intend to use a Certificate Authority to verify your organisation's identity and sign your certificate, you must generate a private key, which is used to create a Certificate Signing Request (CSR), and send the CSR file to the Certificate Authority.
Dec 11, 2016 Create Certificate Sign Request Self Sign CSR. Now The CA get our CSR it will sign our CSR with his private key. But in this example we are CA and we need to create a self-signed key firstly. We create a CA private key named key.pem and certificate named cert.pem which will be used to authenticate the users signed certificate.
To generate the RSA private key, run the following command:
This generates a 2048-bit, RSA private key.
To generate the Certificate Signing Request (CSR), run the following command:
This command prompts for input. Complete the fields as required.
The CN field must correspond to the hostname. It is recommended that you use the fully-qualified server name, rather than localhost.
If you intend to use a self-signed certificate, you can generate the key and certificate with a single command:
This command generates a 2048-bit RSA key, key.pem, and a certificate, cert.pem, which is valid for 365 days.
To install an SSL certificate for the MySQL Enterprise Service Manager:
Save the certificate and private key, both in PEM format, in the following location:

Next, restart the service manager. For more information about stopping and starting the service manager, see the instructions for Unix/Mac OS X and Microsoft Windows.
If you are using a chained certificate implementation, you must add the following attribute to the Connector element of Tomcat's server.xml:
For information on SSL and MySQL Server, see Creating SSL and RSA Certificates and Keys.
To configure SSL-related options for the Agent, the following values may be placed in $INSTALL_ROOT/etc/bootstrap.properties
Table 6.2 SSL Configuration Options For The Agent's bootstrap.properties
| Parameter | Values | Description | Removed |
|---|---|---|---|
|
| Verify that the hostname of the service manager that the Agent is connected to matches what is in the SSL certificate, Default is false, as we are only using SSL for confidentiality | |
|
| https://offshoreplay.weebly.com/home/melodyne-32-mac-download. If set to | |
|
| Default false, but to support self-signed certificates, a commercial certificate, or if the CA certificate has been imported into a keystore, then set to true. | 3.0.20 |
| String | Path to keystore with CA cert(s), if
| |
| String | Password for the CA keystore, if |
An example bootstrap.properties SSL certification section:
To import a CA certificate in PEM format to a new keystore on the Agent, execute the following:
The tool responds with the certificate details. For example:
You must edit the ssl-ca-* configuration values in bootstrap.properties accordingly, to use the path to the keystore and password.
SSL configuration for LDAP is configured at the MySQL Enterprise Service Manager Java VM level. That is, it is configured in the keystore of the Java VM bundled with your MySQL Enterprise Monitor installation.
The JVM shipped with MySQL Enterprise Service Manager does not support the AES256 cipher. This can prevent you using LDAP servers which implement that cipher.
To connect to LDAP servers which implement the AES256 cipher, you must download and install the Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files 8 package. This package is available from: Java Cryptography Extension.
The steps described in this section assume your LDAP server is correctly configured and you have a root CA certificate which was used to generate the LDAP server's certificate.
To enable SSL for LDAP and MySQL Enterprise Service Manager, you must do the following:
Convert the LDAP server's root CA certificate from PEM to DER format, if necessary. If the CA certificate is already in DER format, continue to the next step.
Import the CA certificate, in DER format, into the MySQL Enterprise Service Manager Java keystore. Run the following command from the
bindirectory of your MySQL Enterprise Service Manager's Java installation:Restart MySQL Enterprise Service Manager with the following command:
IoT Edge devices require certificates for secure communication between the runtime, the modules, and any downstream devices.If you don't have a certificate authority to create the required certificates, you can use demo certificates to try out IoT Edge features in your test environment.This article describes the functionality of the certificate generation scripts that IoT Edge provides for testing.
These certificates expire in 30 days, and should not be used in any production scenario.
You can create certificates on any machine, and then copy them over to your IoT Edge device.It's easier to use your primary machine to create the certificates rather than generating them on your IoT Edge device itself.By using your primary machine, you can set up the scripts once and then repeat the process to create certificates for multiple devices.
Follow these steps to create demo certificates for testing your IoT Edge scenario:
- Set up scripts for certificate generation on your device.
- Create the root CA certificate that you use to sign all the other certificates for your scenario.
- Generate the certificates you need for the scenario you want to test:
- Create IoT Edge device identity certificates to test automatic provisioning with the IoT Hub Device Provisioning Service.
- Create IoT Edge device CA certificates to test production scenarios or gateway scenarios.
- Create downstream device certificates to test authenticating downstream devices to IoT Hub in a gateway scenario.
Prerequisites
Linux Generate Cert.pem Key.pem In Hindi
A development machine with Git installed.
Set up scripts
The IoT Edge repository on GitHub includes certificate generation scripts that you can use to create demo certificates.This section provides instructions for preparing the scripts to run on your computer, either on Windows or Linux.If you're on a Linux machine, skip ahead to Set up on Linux.
Set up on Windows
To create demo certificates on a Windows device, you need to install OpenSSL and then clone the generation scripts and set them up to run locally in PowerShell.
Install OpenSSL
Install OpenSSL for Windows on the machine that you're using to generate the certificates.If you already have OpenSSL installed on your Windows device, you may skip this step, but ensure that openssl.exe is available in your PATH environment variable.
There are several ways to install OpenSSL, including the following options:
Easier: Download and install any third-party OpenSSL binaries, for example, from OpenSSL on SourceForge. Add the full path to openssl.exe to your PATH environment variable.
Recommended: Download the OpenSSL source code and build the binaries on your machine by yourself or via vcpkg. The instructions listed below use vcpkg to download source code, compile, and install OpenSSL on your Windows machine with easy steps.
Navigate to a directory where you want to install vcpkg. Follow the instructions to download and install vcpkg.
Once vcpkg is installed, run the following command from a PowerShell prompt to install the OpenSSL package for Windows x64. The installation typically takes about 5 minutes to complete.
Add
<vcpkg path>installedx64-windowstoolsopensslto your PATH environment variable so that the openssl.exe file is available for invocation.
Prepare scripts in PowerShell
The Azure IoT Edge git repository contains scripts that you can use to generate test certificates.In this section, you clone the IoT Edge repo and execute the scripts.
Open a PowerShell window in administrator mode.
Clone the IoT Edge git repo, which contains scripts to generate demo certificates. Use the
git clonecommand or download the ZIP.Navigate to the directory in which you want to work. Throughout this article, we'll call this directory <WRKDIR>. All certificates and keys will be created in this working directory.
Copy the configuration and script files from the cloned repo into your working directory.
If you downloaded the repo as a ZIP, then the folder name is
iotedge-masterand the rest of the path is the same.Enable PowerShell to run the scripts.
Bring the functions used by the scripts into PowerShell's global namespace.
The PowerShell window will display a warning that the certificates generated by this script are only for testing purposes, and should not be used in production scenarios.
Verify that OpenSSL has been installed correctly and make sure that there won't be name collisions with existing certificates. If there are problems, the script output should describe how to fix them on your system.
Set up on Linux
To create demo certificates on a Windows device, you need clone the generation scripts and set them up to run locally in bash.
Clone the IoT Edge git repo, which contains scripts to generate demo certificates.
Navigate to the directory in which you want to work. We'll refer to this directory throughout the article as <WRKDIR>. All certificate and key files will be created in this directory.
Copy the config and script files from the cloned IoT Edge repo into your working directory.
Create root CA certificate
The root CA certificate is used to make all the other demo certificates for testing an IoT Edge scenario.You can keep using the same root CA certificate to make demo certificates for multiple IoT Edge or downstream devices.
If you already have one root CA certificate in your working folder, don't create a new one.The new root CA certificate will overwrite the old, and any downstream certificates made from the old one will stop working.If you want multiple root CA certificates, be sure to manage them in separate folders.
Before proceeding with the steps in this section, follow the steps in the Set up scripts section to prepare a working directory with the demo certificate generation scripts.
Windows
Navigate to the working directory where you placed the certificate generation scripts.
Create the root CA certificate and have it sign one intermediate certificate. The certificates are all placed in your working directory.
This script command creates several certificate and key files, but when articles ask for the root CA certificate, use the following file:
<WRKDIR>certsazure-iot-test-only.root.ca.cert.pem
Linux
Navigate to the working directory where you placed the certificate generation scripts.
Create the root CA certificate and one intermediate certificate.
This script command creates several certificate and key files, but when articles ask for the root CA certificate, use the following file:
<WRKDIR>/certs/azure-iot-test-only.root.ca.cert.pem
Create IoT Edge device CA certificates
Every IoT Edge device going to production needs a device CA certificate that's referenced from the config.yaml file.The device CA certificate is responsible for creating certificates for modules running on the device.It's also how the IoT Edge device verifies its identity when connecting to downstream devices.
Device CA certificates go in the Certificate section of the config.yaml file on the IoT Edge device.
Before proceeding with the steps in this section, follow the steps in the Set up scripts and Create root CA certificate sections.
Windows
Pem Definition
Navigate to the working directory that has the certificate generation scripts and root CA certificate.
Create the IoT Edge device CA certificate and private key with the following command. Provide a name for the CA certificate, for example MyEdgeDeviceCA, which is used to name the output files.
This script command creates several certificate and key files. The following certificate and key pair needs to be copied over to an IoT Edge device and referenced in the config.yaml file:
<WRKDIR>certsiot-edge-device-MyEdgeDeviceCA-full-chain.cert.pem<WRKDIR>privateiot-edge-device-MyEdgeDeviceCA.key.pem
The gateway device name passed into those scripts should not be the same as the 'hostname' parameter in config.yaml, or the device's ID in IoT Hub.The scripts help you avoid any issues by appending a '.ca' string to the gateway device name to prevent the name collision in case a user sets up IoT Edge using the same name in both places.However, it's good practice to avoid using the same name.
Linux
Navigate to the working directory that has the certificate generation scripts and root CA certificate.
Create the IoT Edge device CA certificate and private key with the following command. Provide a name for the CA certificate, for example MyEdgeDeviceCA, which is used to name the output files.
This script command creates several certificate and key files. The following certificate and key pair needs to be copied over to an IoT Edge device and referenced in the config.yaml file:
<WRKDIR>/certs/iot-edge-device-MyEdgeDeviceCA-full-chain.cert.pem<WRKDIR>/private/iot-edge-device-MyEdgeDeviceCA.key.pem
The gateway device name passed into those scripts should not be the same as the 'hostname' parameter in config.yaml, or the device's ID in IoT Hub.The scripts help you avoid any issues by appending a '.ca' string to the gateway device name to prevent the name collision in case a user sets up IoT Edge using the same name in both places.However, it's good practice to avoid using the same name.
Create IoT Edge device identity certificates
Device identity certificates are used to provision IoT Edge devices through the Azure IoT Hub Device Provisioning Service (DPS).
Device identity certificates go in the Provisioning section of the config.yaml file on the IoT Edge device.
Before proceeding with the steps in this section, follow the steps in the Set up scripts and Create root CA certificate sections.
Windows
Create the IoT Edge device identity certificate and private key with the following command:
The name that you pass in to this command will be the device ID for the IoT Edge device in IoT Hub.
The new device identity command creates several certificate and key files, including three that you'll use when creating an individual enrollment in DPS and installing the IoT Edge runtime:
<WRKDIR>certsiot-edge-device-identity-<name>-full-chain.cert.pem<WRKDIR>certsiot-edge-device-identity-<name>.cert.pem<WRKDIR>privateiot-edge-device-identity-<name>.key.pem
Linux
Create the IoT Edge device identity certificate and private key with the following command: Auslogics boostspeed 8 key generator.
The name that you pass in to this command will be the device ID for the IoT Edge device in IoT Hub.
The script creates several certificate and key files, including three that you'll use when creating an individual enrollment in DPS and installing the IoT Edge runtime:
<WRKDIR>certsiot-edge-device-identity-<name>-full-chain.cert.pem<WRKDIR>/certs/iot-edge-device-identity-<name>.cert.pem<WRKDIR>/private/iot-edge-device-identity-<name>.key.pem
Create downstream device certificates
If you're setting up a downstream IoT device for a gateway scenario, you can generate demo certificates for X.509 authentication.There are two ways to authenticate an IoT device using X.509 certificates: using self-signed certs or using certificate authority (CA) signed certs.For X.509 self-signed authentication, sometimes referred to as thumbprint authentication, you need to create new certificates to place on your IoT device.These certificates have a thumbprint in them that you share with IoT Hub for authentication.For X.509 certificate authority (CA) signed authentication, you need a root CA certificate registered in IoT Hub that you use to sign certificates for your IoT device.Any device using a certificate that was issued by the root CA certificate or any of its intermediate certificates will be permitted to authenticate.
The certificate generation scripts can help you make demo certificates to test out either of these authentication scenarios.
Before proceeding with the steps in this section, follow the steps in the Set up scripts and Create root CA certificate sections.
Self-signed certificates
When you authenticate an IoT device with self-signed certificates, you need to create device certificates based on the root CA certificate for your solution.Then, you retrieve a hexadecimal 'fingerprint' from the certificates to provide to IoT Hub.Your IoT device also needs a copy of its device certificates so that it can authenticate with IoT Hub.
Windows
Navigate to the working directory that has the certificate generation scripts and root CA certificate.
Create two certificates (primary and secondary) for the downstream device. An easy naming convention to use is to create the certificates with the name of the IoT device and then the primary or secondary label. For example:
This script command creates several certificate and key files. The following certificate and key pairs needs to be copied over to the downstream IoT device and referenced in the applications that connect to IoT Hub:
<WRKDIR>certsiot-device-<device name>-primary-full-chain.cert.pem<WRKDIR>certsiot-device-<device name>-secondary-full-chain.cert.pem<WRKDIR>certsiot-device-<device name>-primary.cert.pem<WRKDIR>certsiot-device-<device name>-secondary.cert.pem<WRKDIR>certsiot-device-<device name>-primary.cert.pfx<WRKDIR>certsiot-device-<device name>-secondary.cert.pfx<WRKDIR>privateiot-device-<device name>-primary.key.pem<WRKDIR>privateiot-device-<device name>-secondary.key.pem
Retrieve the SHA1 fingerprint (called a thumbprint in IoT Hub contexts) from each certificate. The fingerprint is a 40 hexadecimal character string. Use the following openssl command to view the certificate and find the fingerprint:
Run this command twice, once for the primary certificate and once for the secondary certificate. You provide fingerprints for both certificates when you register a new IoT device using self-signed X.509 certificates.
Linux
Navigate to the working directory that has the certificate generation scripts and root CA certificate.
Create two certificates (primary and secondary) for the downstream device. An easy naming convention to use is to create the certificates with the name of the IoT device and then the primary or secondary label. For example:
This script command creates several certificate and key files. The following certificate and key pairs needs to be copied over to the downstream IoT device and referenced in the applications that connect to IoT Hub:
<WRKDIR>/certs/iot-device-<device name>-primary-full-chain.cert.pem<WRKDIR>/certs/iot-device-<device name>-secondary-full-chain.cert.pem<WRKDIR>/certs/iot-device-<device name>-primary.cert.pem<WRKDIR>/certs/iot-device-<device name>-secondary.cert.pem<WRKDIR>/certs/iot-device-<device name>-primary.cert.pfx<WRKDIR>/certs/iot-device-<device name>-secondary.cert.pfx<WRKDIR>/private/iot-device-<device name>-primary.key.pem<WRKDIR>/private/iot-device-<device name>-secondary.key.pem
Retrieve the SHA1 fingerprint (called a thumbprint in IoT Hub contexts) from each certificate. The fingerprint is a 40 hexadecimal character string. Use the following openssl command to view the certificate and find the fingerprint:
You provide both the primary and secondary fingerprint when you register a new IoT device using self-signed X.509 certificates.
CA-signed certificates
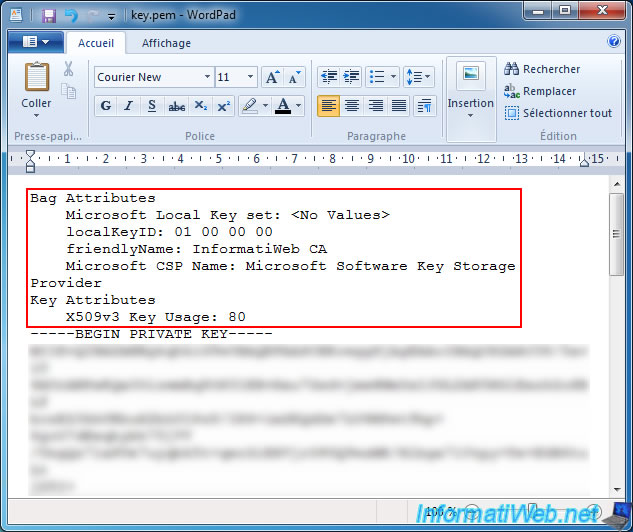
When you authenticate an IoT device with self-signed certificates, you need to upload the root CA certificate for your solution to IoT Hub.Then, you perform a verification to prove to IoT Hub that you own the root CA certificate.Finally, you use the same root CA certificate to create device certificates to put on your IoT device so that it can authenticate with IoT Hub.
The certificates in this section are for the steps in Set up X.509 security in your Azure IoT hub.
Windows
Upload the root CA certificate file from your working directory,
<WRKDIR>certsazure-iot-test-only.root.ca.cert.pem, to your IoT hub.Use the code provided in the Azure portal to verify that you own that root CA certificate.
Create a certificate chain for your downstream device. Use the same device ID that the device is registered with in IoT Hub.
This script command creates several certificate and key files. The following certificate and key pairs needs to be copied over to the downstream IoT device and referenced in the applications that connect to IoT Hub:
<WRKDIR>certsiot-device-<device id>.cert.pem<WRKDIR>certsiot-device-<device id>.cert.pfx<WRKDIR>certsiot-device-<device id>-full-chain.cert.pem<WRKDIR>privateiot-device-<device id>.key.pem
Linux Generate Cert.pem Key.pem File
Linux
Linux Generate Cert.pem Key.pem Free
Upload the root CA certificate file from your working directory,
<WRKDIR>certsazure-iot-test-only.root.ca.cert.pem, to your IoT hub.Use the code provided in the Azure portal to verify that you own that root CA certificate.
Create a certificate chain for your downstream device. Use the same device ID that the device is registered with in IoT Hub.
This script command creates several certificate and key files. The following certificate and key pairs needs to be copied over to the downstream IoT device and referenced in the applications that connect to IoT Hub:
<WRKDIR>/certs/iot-device-<device id>.cert.pem<WRKDIR>/certs/iot-device-<device id>.cert.pfx<WRKDIR>/certs/iot-device-<device id>-full-chain.cert.pem<WRKDIR>/private/iot-device-<device id>.key.pem